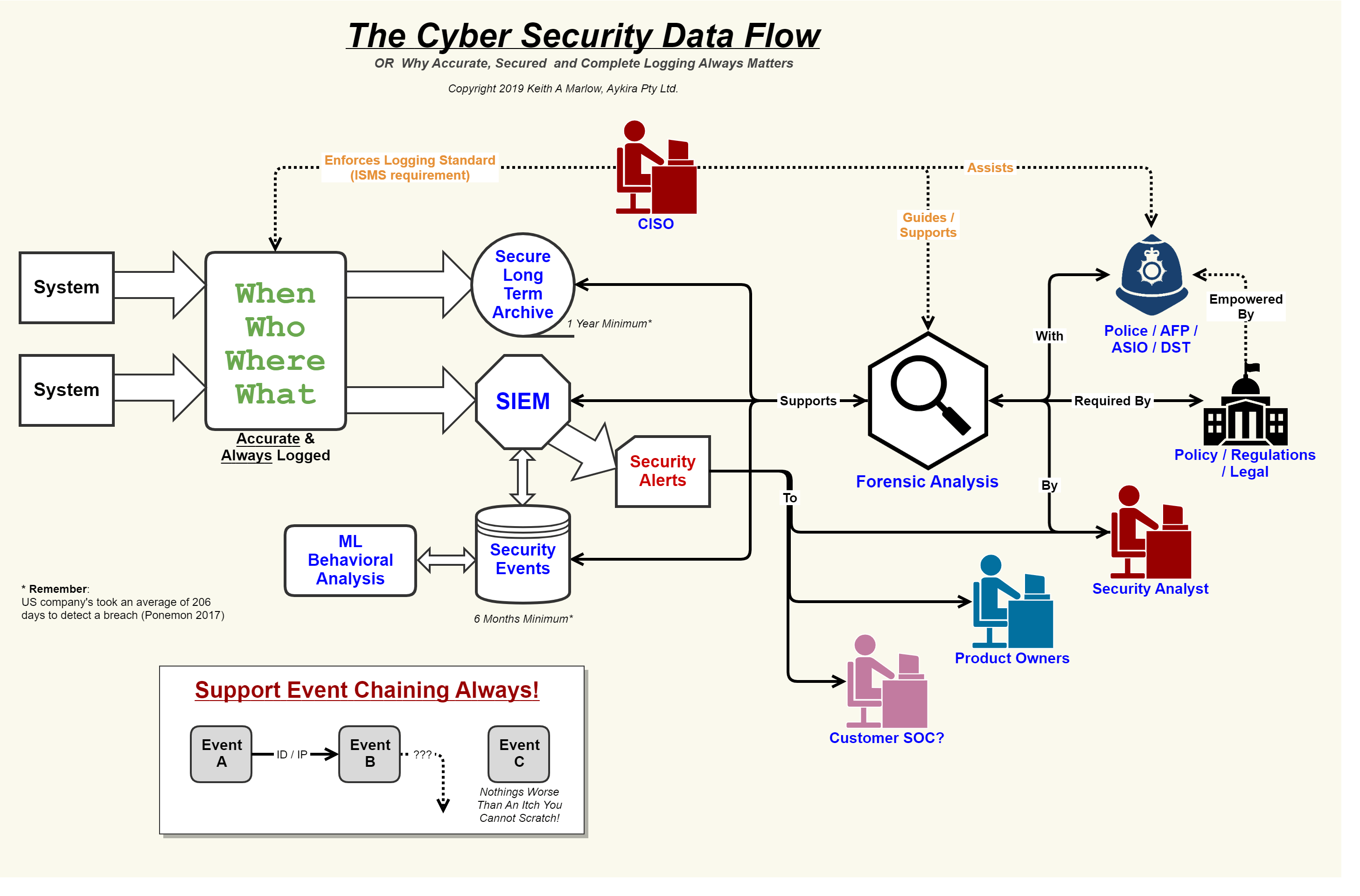
Security architecture Security event logging, why it is so important – aykira internet solutions Cybersecurity in 2022-2023: protecting our digital world cybersecurity system architecture diagram
Cyber Security Architecture and its Benefits
Everything you need to know about ai cybersecurity Cybersecurity reference architecture: security for a hybrid enterprise Cyber security architecture and its benefits
Use gartner cybersecurity research & insights to develop your ideal
Cybersecurity frameworks — types, strategies, implementation andBest infographics on twitter Network security diagram firewall wireless computer wan diagrams secure lan architecture networks example networking drawing between clipart conceptdraw system cyberResponsibilities cybersecurity roles framework function organize cyber azure ciso governance functions compliance desai rahul funciones culture adoption defending adversaries.
Understanding the 3 phases of cybersecurity architectureApplied sciences Cybersecurity areas network information focus aloha secure20+ cyber security diagrams.

Components of cybersecurity
Security architecture, enterprise architecture, data securityWhat is cybersecurity architecture and why is it important? — zengrc Cyber security degreesCybersecurity cyber layered capas perimeter profundidad defensa plataformas infographics fisher sistemas ataque seguros realmente mis.
Network security diagramsPin on chalkpiece Modern cybersecurity architectureWhat is a cyber security architecture? importance, diagram.

Cyber security framework
Security enterprise architecture cybersecurity cyber reference linkedin microsoft office information protection saved data digital softwareSse: the mvp of the cybersecurity mesh architecture Cybersecurity types frameworks strategies security framework controls implementation cis critical they has defined three benefits ape europe environment basic variousCyber security diagram.
How to organize your security team: the evolution of cybersecurityIot & enterprise cybersecurity Cybersecurity map domains henry jiang mindMicrosoft cybersecurity reference architectures.
.png)
Pin on computer security
Architecture cybersecurity modernSecurity flow data cyber event logging diagram internet logs important why so together showing concerning events au putting Cybersecurity frameworks and information security standardsCybersecurity roadmap capabilities compliance atp infrastructure document m365 mcra digital.
Security network diagram architecture example cyber firewall computer diagrams clipart conceptdraw recommended model networks microsoft secure draw management solution structureRelated keywords & suggestions for network security firewall Cyber security architecture diagramCyber security framework mind map template.

Architecture cybersecurity enterprise iot cyber security diagram system software
Cybersecurity domains mind mapSecurity cyber network tips cybersecurity computer infographic steps diagram degrees diagrams example conceptdraw networks solutions architecture information risks threats examples .
.